Hardware & Proxmox Setup for Purple Team Lab - Part One in Cyber Lab Series
Introduction#
Want to sharpen your pentesting and blue team skills in 2025? Setting up a cybersecurity lab at home is the ultimate hands-on training ground. In Part One of this series, I’ll walk you through the hardware, initial Proxmox setup, and network configuration with fixes from my own lab woes (e.g., a misconfigured /etc/network/interfaces). Whether you’re troubleshooting VLANs or prepping for Security Onion, this guide’s got you covered.
Changes#
This article was updated on 3/5/2025
This article has an updated /etc/network/interfaces file, there were some
serious misconfigurations in there, but regardless of that my network was
working which is why I didn’t think my interfaces file had any issues. I
discovered this was an issue in my most recent article when setting up the
Cuckoo VM subnet. The “address” sections for all VLANs under and including
vmbr1 was configured to a subnet instead of an individual static IP (leading to
the gateway interface of the pfSense VM). vmbr1 itself does not need an IP as
it is a “manual” bridge interface, so that is reflected in the new interfaces
file as well.
post-up for i in rx tx sg tso ufo gso gro lro; do ethtool -K vmbr1 $i off; done
Also note the command above (unchanged from the previous configuration) is meant for Security Onion, here’s an explanation:
If Security Onion is running as a VM on Proxmox and monitoring network traffic through vmbr1 or its VLAN subinterfaces. Here’s why:
Improved Packet Capture Accuracy: Disabling offloads ensures that Security Onion’s packet analysis tools (Suricata, Zeek, Stenographer, etc.) receive unfragmented, un-reassembled packets as they appear on the wire. This prevents issues like incomplete packet captures, IDS evasion, or misinterpretation of traffic, which are critical for threat hunting and network security monitoring.
Alignment with Best Practices: Security Onion’s documentation and community (e.g., blog posts from 2011 and later) explicitly recommend disabling network offload features (e.g., TSO, GSO, GRO, LRO) on network interfaces used for packet capture to ensure “full packet capture.” The post-up command you’re using aligns with this practice, as it’s a common method to disable offloads at boot time.
Avoiding Evasion/Insertion Attacks: As noted in Security Onion blogs, offloads can allow attackers to manipulate packet reassembly, potentially evading detection by IDS/IPS systems like Suricata. Disabling offloads mitigates this risk by ensuring Security Onion sees the same packets as the destination host.
This article was updated on 6/23/2024
- [Updated the network map]
- [Updated network switching instructions]
- [Corrected and updated my /etc/network/interfaces configuration for Proxmox]
Why Build a Cybersecurity Lab at Home?#
As a cybersecurity or IT professional, it is paramount that we keep our skills up to date. Regarding training, there’s many resources out there, but in my opinion the best way to train yourself is to build something from the ground up. What you build doesn’t have to be an advanced XDR it can be something simpler like what I’m working on. Technology at the fundamental level hasn’t really changed. The new security solutions that come out everyday work the same fundamentally. Building simpler projects that are based on more complex production ready products is a great way to learn how a security/IT solution works, this process of learning is applicable to most new products that come out.
My Lab Journey - From Layoff to Learning#
Building my purple teaming lab is what I decided to do during my layoff. Instead of sitting around waiting for something to happen and allowing my skills to grow dull, I decided to take initiative to grow as a person and a professional. This home lab has helped me to persevere and discipline myself when problem solving and troubleshooting is hard.
Building persistence is the key to becoming a good problem solver.
I used the classic troubleshooting methodology of recognizing where I was at on the OSI layer and going up or down the stack depending on what kind of problem I was facing that needed resolution. For example, just last night I didn’t understand why my Windows 2019 Server DC was not getting an Internet connection. I noticed the network adapters had a red x on them. I started troubleshooting at Layer 3 (Networking/Routing), I managed to ping the AD-DC gateway, but obviously could not ping the DC. I recognized the adapters were not even available on the Windows DC so this was a layer 1 or layer 2 issue. After some research I needed to install Proxmox specific network drivers for Window guests, once I loaded the driver iso onto the VM and installed them, the networking adapters were online and I could finally ping to the DC.
When I managed to solve a problem, it was a victory, whether big or small it kept me motivated to stay on this path of self-training.
Part One covers the hardware needed, initial setup and networking configuration on Proxmox.
Hardware You’ll Need for Your Cyber Lab#
- [Workstation (64 GB RAM and 2TB of space). I used this Lenovo ThinkCentre M900
- [Networking Switch (has at least 4 free ports). I used this RB260GS MikoTek Switch
- [Home Router (mine has 1GB of internet speed). I used an ARRIS G34
Before we build the lab, we need a plan. I suggest creating a network map like the one I made. This network map will evolve as we progress through this home lab series.
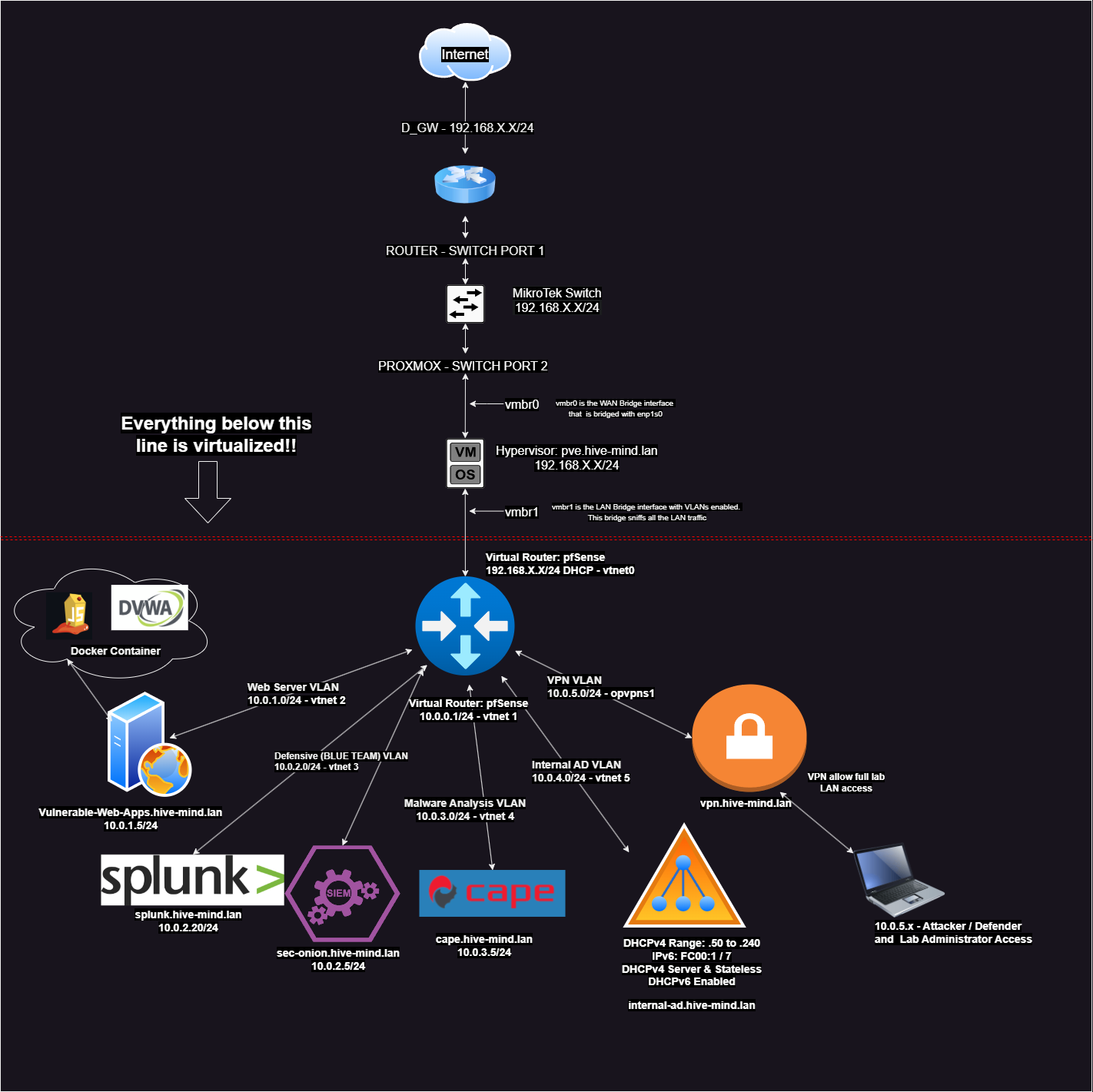
Step-by-Step Proxmox Setup#
Download and Flash Proxmox VE 8.1#
- Download the Proxmox VE 8.1 ISO and have it flashed onto a USB drive: https://www.proxmox.com/en/downloads/proxmox-virtual-environment/iso/proxmox-ve-8-1-iso-installer
- Plug one ethernet port of the switch into the router, and the second switch port into your Workstation running the Proxmox Hypervisor.
- Flash the Proxmox iso onto your workstation hardware using a USB stick.
- Access the Proxmox web interface at
https://[IP-address]:8006You may have to login to your router to see what IP address Proxmox is assigned to. - While on the router console find out what your switch IP is if you don’t know it.
- Your switching configuration should have auto negotiation enabled on ports one and two. Auto negotiation is a very helpful feature to have on your switch as these two switch ports will determine optimal duplex mode and connection speeds. Its optional, but I turned off the ports I wasn’t going to be using.

Configure Proxmox Networking#
- On the Proxmox web interface, go to the pve shell and edit your interfaces file.

Here’s what my Proxmox /etc/network/interfaces file looks like:
auto lo
iface lo inet loopback
auto enp1s0
iface enp1s0 inet manual
auto vmbr0
iface vmbr0 inet static
address 192.168.0.50/24
gateway 192.168.0.1
bridge-ports enp1s0
bridge-stp off
bridge-fd 0
# Bridge with VLANs enabled
auto vmbr1
iface vmbr1 inet manual
bridge-ports none
bridge-stp off
bridge-fd 0
bridge-vlan-aware yes
bridge-vids 2-4094
post-up for i in rx tx sg tso ufo gso gro lro; do ethtool -K vmbr1 $i off; done
# Vulnerable Web Server VLAN
auto vmbr1.10
iface vmbr1.10 inet static
address 10.0.1.1
netmask 255.255.255.0
vlan-raw-device vmbr1
# Security Onion and Splunk subnet (other Blue Team related devices as well)
auto vmbr1.20
iface vmbr1.20 inet static
address 10.0.2.1
netmask 255.255.255.0
vlan-raw-device vmbr1
# Malware Analysis subnet with Cuckoo VM
auto vmbr1.30
iface vmbr1.30 inet static
address 10.0.3.1
netmask 255.255.255.0
vlan-raw-device vmbr1
# Windows AD Network with DC(s) and Hosts
auto vmbr1.40
iface vmbr1.40 inet static
address 10.0.4.1
netmask 255.255.255.0
vlan-raw-device vmbr1
Detour! – What’s a VLAN?#
A VLAN (Virtual LAN) segments network traffic on Proxmox (e.g., vmbr1.10 for web servers, vmbr1.20 for the Blue Team subnet, vmbr1.40 for vulnerable Active Directory, etc.) for isolation, security, and organization—keeping pentesting and blue team VMs separate.
Detour! – Why disable TSO?#
Disabling TSO (TCP Segmentation Offload) on vmbr1 ensures Security Onion captures raw, unprocessed packets, preventing IDS evasion and ensuring accurate threat detection in your lab’s traffic sniffing.
Note the post-up commands in the interfaces file exist so that SecurityOnion can sniff traffic from Proxmox’s virtual NIC. In our case we will use vmbr0 (bridged with enp1s0) as our WAN bridge connected to the Internet. vmbr1 will be used as the LAN bridge that is sniffing network traffic from each VLAN under it. Here’s more information on virtual NIC sniffing: https://docs.securityonion.net/en/2.4/proxmox.html
After the edits you should reload the networking configuration with
ifreload -athe changes should persist since we saved the changes to the interfaces file.The Proxmox “pve” Network tab should show the new configuration once your interfaces file has been reloaded.

Back to Full Series.
If you found my content valuable, support me here to help me make more content for the cybersecurity community: https://buymeacoffee.com/phoenix.educatum