Setup Security Onion and Active Directory for 2025 - Part Three in Cyber Lab Series
In this part, I will show you how to setup the Security Onion SOC/SIEM and the
endpoints that need to be monitored. In the next article we setup Splunk as our
SIEM. As a pre-requesite for this article it is assumed you already have your
endpoints configured and ready for Security Onion elastic agent endpoint .msi
installations.
All of these parts have instructions that are cumulative for the home lab. You should be familiar with part one and part two before applying the instructions in part three (this article). If you haven’t already, check out part one and part two in this cyber home lab creation series.
Download ISO and VM Creation#
Download the Security Onion ISO from GitHub
Create the Security Onion VM

See the Security Onion hardware requirements: https://docs.securityonion.net/en/2.4/hardware.html
I chose the standalone deployment therefore:
- [Instead of the recommended 24GB of ram, I configured almost 28GB]
- [4 CPU cores]
- [500GB of storage, instead of the recommended minimum of 200GB]
Regarding networking:
- [The first interface is vmbr1 (which is the sniffer bridge for the entire LAN network).]
- [The second interface (vmbr1.20) is the management interface which exists on its own VLAN.]
Installation Steps#
Clarification: The steps below were done on Security Onion 2.3.290. But since then I have redone these steps on Security Onion 2.4.70. The installation steps are almost the same.

- Pick username/password
Pick whatever username/password you can remember. Obviously change the username and make the password secure if you’re using this in production!!!

Log in with your credentials and you will see this screen:

I recommend configuring networking first.

- Pick whatever hostname you like. Just make it memorable for configuration in upcoming steps.

Remember the Proxmox networking configuration in part one of our series:
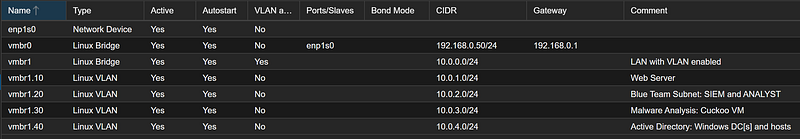
- Select your managed NIC to be
eth1(vmbr1) since vmbr1.20 VLAN in within vmbr1.eth0(vmbr0) is the monitored NIC and it does not have an IP address.

- Setup static addressing.
Pick an address that is within your vmbr1.20 VLAN subnet that we configured during pfSense setup in part two. In my case I picked 10.0.2.5.

- Configure gateway IP address
This is the gateway address that your pfSense VM is directly responsible for within your Blue Team VLAN.


- Setup DNS
I used the CloudFlare DNS servers.

- Setup search domain
My search domain is hive-mind.lan


- Decide your type of Installation
I picked standalone, but you may pick a different option depending on your needs.

The other installation steps are straightforward. One important thing to note is that the VPN subnet (10.0.5.0/24) should be added when asked for “Allowed IP or Subnet”, see final installation parameters below.
If you’re having issues with networking and need to run the installation again in the Security Onion command line console. This documentation may also help: https://docs.securityonion.net/en/2.4/proxmox.html
sudo SecurityOnion/setup/so-setup iso
If you’re still having issues with Security Onion not communicating with the pfSense router, I suggest troubleshooting by going up the OSI layer, starting at the physical layer (the NICs) and up to the application layer (DNS, HTTP, DHCP etc). For example a physical layer issue could be something simple such as you forgetting to plug in an ethernet cord from your switch to your router or from your switch to your Proxmox hardware. One network layer issue may be the router not being configured properly and you’re missing a default gateway for the Security Onion VLAN.
Here are my final installation parameters:

From my previous post in this home lab creation series, we know that vmbr1 is the bridge that sniffs the entire LAN.


If for whatever reason, eth0 was not configured during the installation to be the monitoring (sniffing/mirrored) NIC it can be added into Security Onion’s shell with the command below
sudo so-monitor-add eth0
eth1 is our Security Onion’s IP (the red box) and that IP will be used when we access Security Onion’s SOC interface on our browser.
Configuring Access to the SOC Console#
Connect to the VPN we created in part two.
The VPN subnet (10.0.5.0/24) has to be allowed through the security onion firewall. Remember, your main way to access your home lab is through the VPN we had defined with the firewall rules in part two of our home lab series.
sudo so-firewall includehost analyst <YOUR-VPN-IP>
Our SOC firewall rules need to be configured to allow three subnets on the console. Subnets (or individual IPs) also need to be added as endpoints that will be reporting to the Security Onion SOC.
For now, we are collecting logs from the Windows AD subnet and Vulnerable Web Server subnet. For firewall rules, we are allowing the Windows Victim and Vulnerable Web Server subnet alongside the VPN subnet through the firewall.
Note: we will configure the vulnerable web server subnet in a later article as the Linux container requires different steps.
This video is a good guide in setting up security onion endpoints:
https://www.youtube.com/watch?v=cGmQMsFuAvw&ab_channel=SecurityOnion
We allow the Vulnerable Web Server and Windows AD VLANs to send logs to Security Onion. If adding the subnets does not allow logs to come through, try adding the individual IPs (as a temporary solution).


After adding the elastic endpoint subnets, allow the vulnerable web server, Windows AD VLAN, and VPN subnets through the security onion firewall.
Alongside the Vulnerable Web Server and Windows AD VLAN we allow our VPN network through the firewall.

“Synchronize Grid” again. Give it about 5–10 minutes before downloading the installer files next.
Next we have to setup the endpoints that Security Onion will be monitoring.
Endpoint Setup#
Pre-requisites#
Download the installation media and follow the steps to create an ISO.
Load the proxmox drivers ISO into Proxmox’s database:

Creating the Windows DC “Hive-Mind”#
Make sure to boot up the Windows DC with the ISO and these hardware requisites:

The Windows_Server_2019.iso and Proxmox windows guest tools iso are loaded.
The virtio toolkit helps with copy/pasting. Allowing cache write back to the
processor and this improves performance.
For networking we have VLAN 40 on the subnet 10.0.4.0/24.
Active Directory DC Setup#
Change the PC Name

Elevate Server to a Domain Controller
- Click “Manage” and then “Add Roles and Features”

Click “next” in the wizard and make sure “role-based or feature based” installation is selected.
When you come to the Select server roles window, make sure to select Active Directory Domain Services, and then click “Add Features”

- Keep clicking next and at the “Confirm installation selections” check “Restart the destination server automatically if requires.” Then click “yes” and “Install”

Click on “Promote this server to a domain controller”.
Specify root domain name. I used “hive-mind.lan” for my lab.

- On the next screen, enter a simple password you can remember (as this is an intentionally vulnerable AD lab!), keep it the same as your Admin password. We will be brute forcing and exploiting these passwords later on.
Your domain name should populate on the next screen
Once you pass the “Prerequisites Check”, click “Install”
After you reboot, log back in, you should see the server manager dashboard.
Click on
Manage->Add roles and features->Click nextand make sureRole-based or feature-based installationis selected->Click nextuntil you get to server roles.On server roles make sure you select
Active Directory Certificate Services. This role is used to verify identities in a domain controller, enhances security and allows use ofLDAP[S]ecure. LDAP is needed for an AD build.

Click Next until you reach the “Confirmation” window and select the option to restart your DC and then click “Install.”
Once installation is finished click on
Configure Active Directory Certificate Services on the destination server.Click
Next, selectCertification Authorityand keep clickingnextaccepting the defaults.Set the validity period for a long time. Like
80years for example.Get to the confirmation page, click
Configureand reboot.
Install Proxmox Guest Tools on the Domain Controller#
Double click virtio-win-gt-x64, most likely your Windows Server installation
is 64 bit and not 32 bit so click on the x64. If it is 32 bit click on the
x86 version.

Windows DC (RDP) (Optional)#
I recommend enabling RDP on your new Windows DC for remote management as this makes everything much easier. My Windows Server VM was pretty sluggish so I used RDP to manage my Windows Server through my lab VPN.

Make sure RDP is enabled

Connect to your VPN first and then RDP to your AD-DC from your Windows box.
Setup AD DNS#
Open up DNS Manager
Right-click
Reverse Lookup Zonesin the left panel and selectNew Zone

- Follow the default settings recommended in the wizard until you are prompted for a Network ID, for which you should use the first three parts or octets of your Active Directory subnet address.

- After we create the zone we have to create a PTR record.
If you want to know your DC hostname definitively, type “hostname” in your command prompt.
Click Create New Pointer (PTR) with the following Name: IP of your DC and Data is the hostname of your DC and then your local domain name in this format: domain.tld.

Creating the Windows Desktop “Drones”#
For Windows 10 Pro download the installation media and follow the directions
You may need the virto drivers (in iso format) for your drives to be seen by the Windows installation software.
If you haven’t already, make sure you download the virtio drivers and load them into your Proxmox ISO storage: https://fedorapeople.org/groups/virt/virtio-win/direct-downloads/latest-virtio/virtio-win.iso
You also have to load the virtio ISO as an additional drive, see the
screenshot below.
- On your Proxmox Hypervisor, click
Create Virtual Machine.
Note: The options in the yellow are highly recommended as your Windows installation may need the drivers for the Proxmox hard disk to be “seen” by the Windows installation ISO.



- Enabling
Write backon the cache helps with performance.



This is part of the Victim AD subnet (vmbr1.40) / VLAN 10.0.4.0/24.

Confirming configuration

- Power on your VM and run through the installation steps, you don’t need a product key, go on without it, and select Windows 10 Pro.

- Accept the License terms and click “Custom”

4a. If your allocated disk space doesn’t show up, we would have to load the virtio driver that we mounted alongside the iso in the new VM configuration.
A reminder of our previous step




Scroll down to the pass-through controller drivers


 You should get to this screen.
You should get to this screen.

- Let the installation finish, log on to your windows desktop and install the virtio drivers as Admin.

- Check if the windows endpoint can
pingthe Security Onion SIEM IP.

Join Windows 10 Endpoint to the Hive-Mind AD#


- Enter Domain Admin credentials (created on the Windows 2019 server)


Connect to DC DNS Server#
Pointing Windows 10 to Windows Server DC as DNS Server

Windows Endpoint Logging Configuration#
The Windows 10 computers and Windows 2019 server need to be configured for monitoring with the Security Onion SOC. We need to download the installer files from the Security Onion Console, transfer it to our endpoints with a USB mapping through Proxmox and download it on the Windows devices to run the installers.
- We have to download these files for Windows:

Download the files to your host machine onto your USB.
Plug in our USB on the PVE hardware running Proxmox.

Click Add

Add the USB Hardware onto our Windows 2019 Server VM

On your Windows 2019 Server VM, you should be able to initiate the install.
- Make sure to run the elastic agent
.exeas an administrator


Go to your security onion dashboard and you should see your AD-DC sending logs:

Side note: I was having issues with time syncing to my time zone on my Windows 2019 server, I used these commands to make it work:
w32tm /query /status
w32tm /unregister
net stop w32time
w32tm /register
net start w32time
w32tm /config /syncfromflags:manual /manualpeerlist:"0.us.pool.ntp.org,1.us.pool.ntp.org"
net stop w32tm && net start w32tm
w32tm /query /source w32tm /query /configuration
I rebooted to let the changes take effect.
Repeat the same endpoint configuration steps as above on the Windows 10 endpoint. You have to run the elastic agent with admin privileges and then check your Security Onion SOC console to see if the endpoint is sending events.
Back to Full Series.
References#
Security Onion Walkthrough on Youtube
Windows VirtIO Drivers – VirtIO Drivers are paravirtualized drivers for kvm/Linux
https://pve.proxmox.com/wiki/Windows_VirtIO_Drivers
https://fedorapeople.org/groups/virt/virtio-win/direct-downloads/latest-virtio/virtio-win.iso
https://download.securityonion.net/file/securityonion/securityonion-2.4.70-20240529.iso
If you found this article helpful and want to support me in my content creation then buy me a coffee